Generating a token
OAuth 2.0 Token Generation
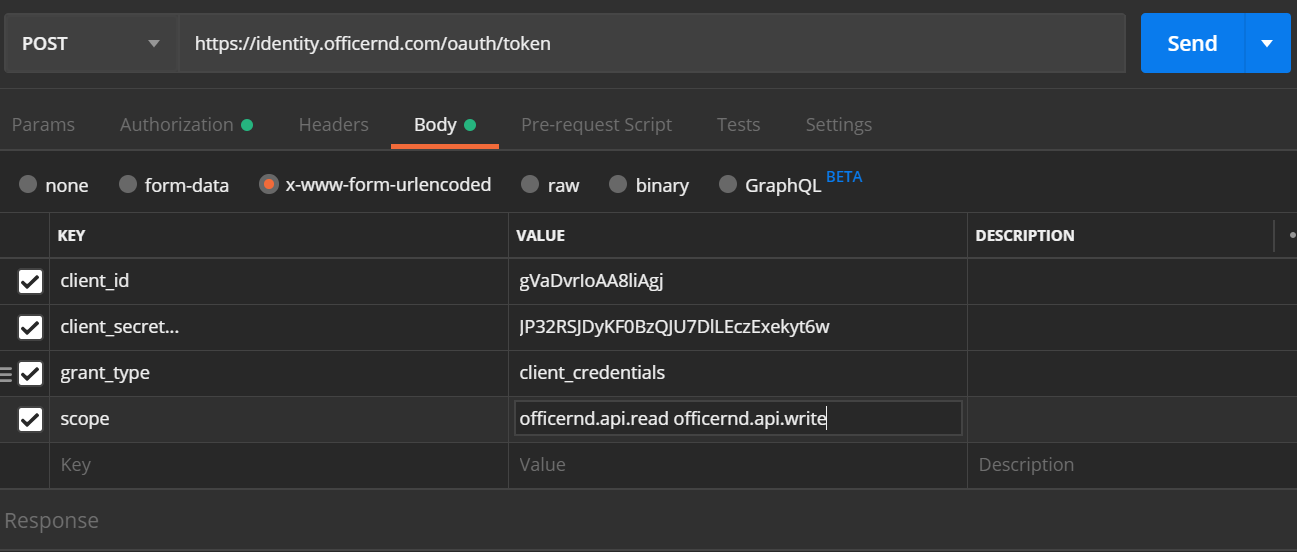
Now that you have your Client ID and Client secret, you can make a call to the OfficeRnD API to generate a token.
Token Generation Endpoint
The URL for generating a token is:
https://identity.officernd.com/oauth/tokenRequest Details
Request Method
- Method: POST
- Content-Type Header:
application/x-www-form-urlencoded
Request Body Parameters
| Parameter | Description |
|---|---|
client_id | Taken from the OfficeRnD application you created |
client_secret | Taken from the OfficeRnD application you created |
grant_type | Currently only supports "client_credentials" |
scope | Fine-grained permissions that limit what the token can do |
NoteThe token will respect the permissions specified for the application. For example, an application with only "Read" permissions cannot generate a token with "Create" permissions.
ImportantCORS is disabled for security reasons.
It is recommended to exchange app secrets for an access token through a server application (Node.js, Python, Go, .NET) or cURL requests where credentials can be stored securely.
Postman Example
Token Response
After sending the POST request, you'll receive a response with the following structure:
{
"access_token": "<access_token>",
"token_type": "Bearer",
"expires_in": 3599,
"scope": "officernd.api.read officernd.api.write"
}Key points:
- All tokens are valid for 3600 seconds (1 hour)
expires_inspecifies the remaining time in seconds
Example Request and Response
cURL Request
curl -X POST \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "client_id={client_id}&client_secret={client_secret}&grant_type=client_credentials&scope=officernd.api.read officernd.api.write" \
https://identity.officernd.com/oauth/tokenResponse
{
"access_token": "{access_token}",
"token_type": "Bearer",
"expires_in": 3599,
"scope": "officernd.api.read officernd.api.write"
}Using the Authorization Header
Add the Authorization header to every request:
Authorization: Bearer <access_token>You can also generate a token here.
Updated 6 months ago
What’s Next